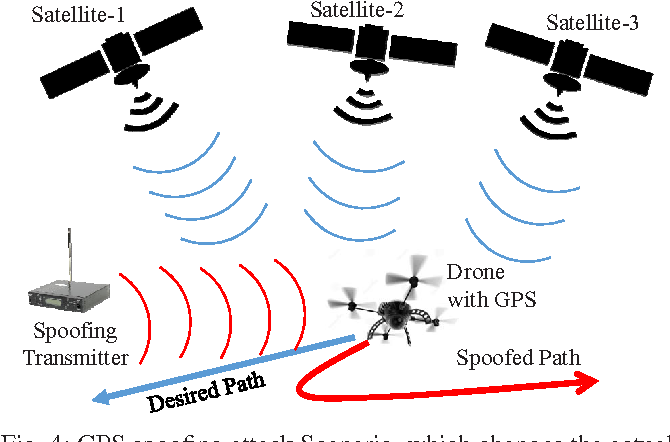
Remote Sensing | Free Full-Text | ConstDet: Control Semantics-Based Detection for GPS Spoofing Attacks on UAVs
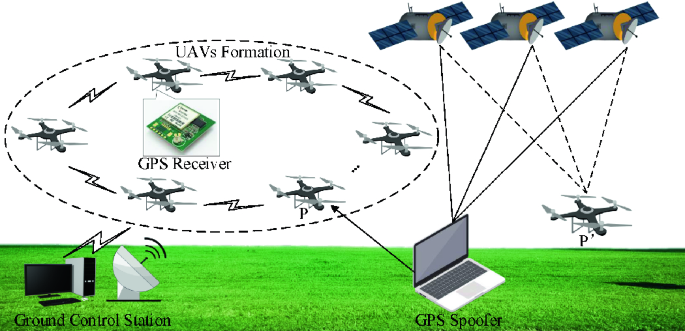
![On GPS spoofing of aerial platforms: a review of threats, challenges, methodologies, and future research directions [PeerJ] On GPS spoofing of aerial platforms: a review of threats, challenges, methodologies, and future research directions [PeerJ]](https://dfzljdn9uc3pi.cloudfront.net/2021/cs-507/1/fig-5-2x.jpg)
On GPS spoofing of aerial platforms: a review of threats, challenges, methodologies, and future research directions [PeerJ]
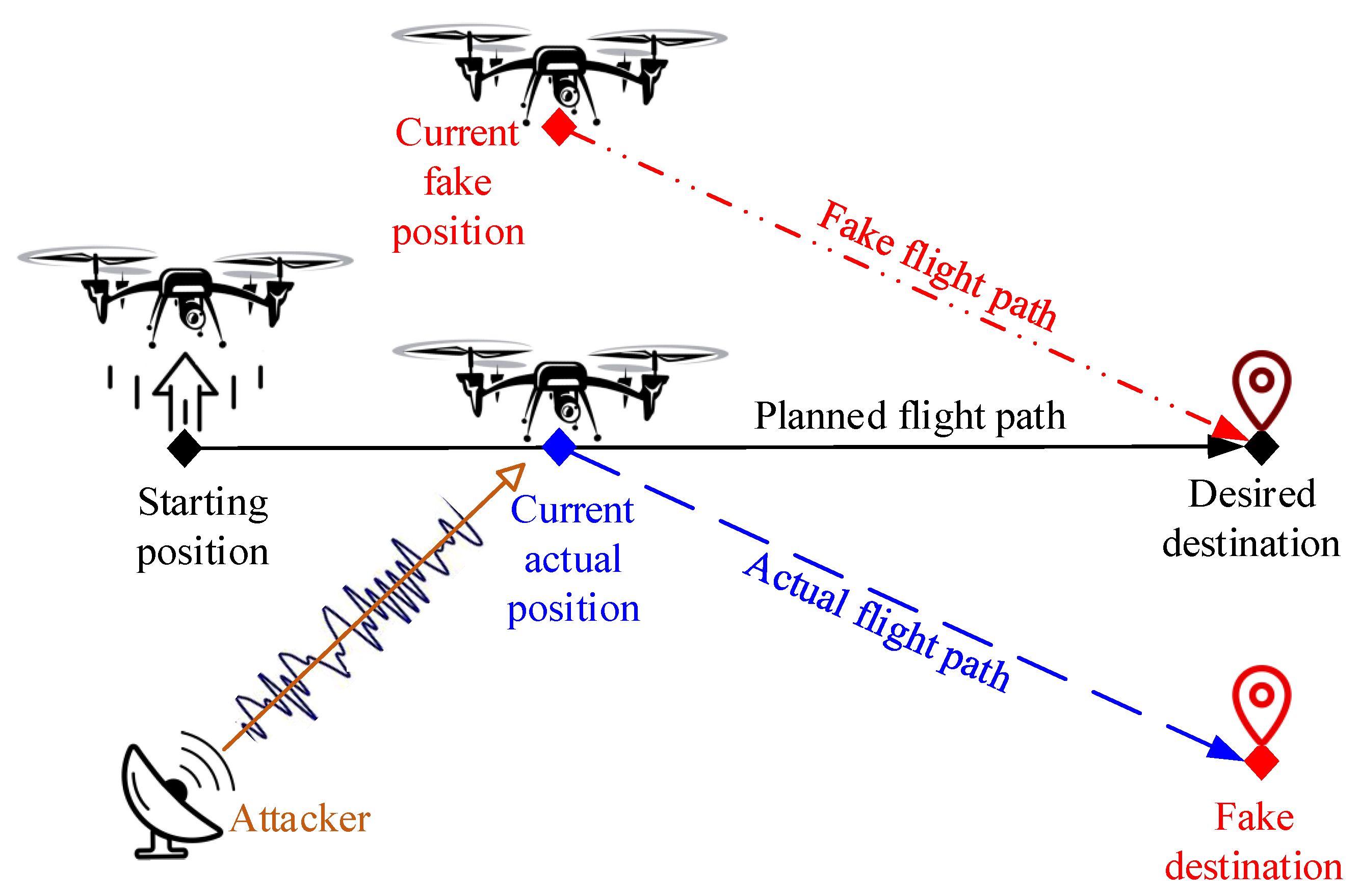
![On GPS spoofing of aerial platforms: a review of threats, challenges, methodologies, and future research directions [PeerJ] On GPS spoofing of aerial platforms: a review of threats, challenges, methodologies, and future research directions [PeerJ]](https://dfzljdn9uc3pi.cloudfront.net/2021/cs-507/1/fig-4-full.png)
On GPS spoofing of aerial platforms: a review of threats, challenges, methodologies, and future research directions [PeerJ]

Sensors | Free Full-Text | GPS Spoofing Detection Method for Small UAVs Using 1D Convolution Neural Network
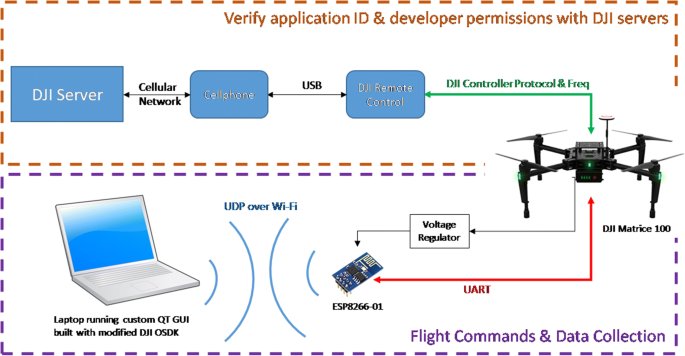
Development of a GPS spoofing apparatus to attack a DJI Matrice 100 Quadcopter | The Journal of Global Positioning Systems | Full Text

UAVs Vulnerable to Civil GPS Spoofing - Inside GNSS - Global Navigation Satellite Systems Engineering, Policy, and Design